Tactical Privacy Wire #18

June 9, 2025
Fast actionable privacy intel for people who live at risk.

🔴THE THREAT LANDSCAPE🔴
Privacy Quake
Urgent, high-priority info. Active exploits, major doxxing incidents, geopolitical tech shifts.
🔴 Meta & Yandex Are De-Anonymizing Android Web Users
Ars Technica
New research shows Meta and Yandex are bypassing core mobile security principles by breaking the sandbox between apps and web browsers. Through an attack vector that passes cookies and unique identifiers from Firefox and Chromium-based browsers to native Android apps (like Facebook, Instagram, and Yandex apps), they are able to link extensive browsing history to specific user accounts.
Why this matters: Sandboxing is supposed to prevent this. By collapsing the web-app boundary, these companies gain massive surveillance power over Android users’ behavior - even across "private" browsing contexts. It’s a fundamental erosion of user anonymity.
Key takeaway: If you're an Android user, assume your web activity is being tied to your app identities.
Harden your defenses: hardened browsers, firewalling, and minimizing app usage linked to personal accounts.
DARK SIGNALS
New, evolving, or resurgent privacy/security threats.
🔴 I Bought a Used Tesla - And Got Remotely Hijacked
TorqueNews
A new Tesla owner was trapped in a surreal battle of digital control after buying a used Model S. The previous owner retained mobile app access and used it to lock the car in valet mode, drain the battery, trigger the horn, and control heating/cooling systems. All remotely.
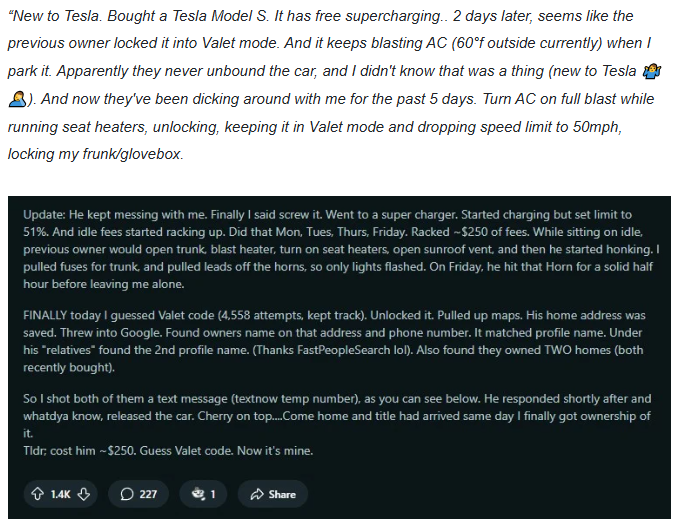
This is not an isolated incident. Increasingly, IoT-linked vehicles and smart devices retain ghost owner access after resale or transfer.
Key takeaway: Before buying used connected tech:
- Verify transfer of digital ownership (Tesla makes this hard).
- Audit and revoke all lingering permissions.
- If needed, physically isolate the device (disconnecting antennas, removing batteries) until verified safe.
In this case, the new owner had to brute-force the valet PIN and rack up $250 in idle fees to force resolution. Expect more of this in an era of "software-defined ownership."
TERMS OF ABUSE
Public failures of data stewardship.
🔴 Meta Moves to Dismiss Lawsuit Alleging Unauthorized Location Data Collection via Mobile Apps
Meta is facing a class-action lawsuit alleging that its Facebook Audience Network software embedded in thousands of mobile apps secretly collected precise location data from users - even when location services were turned off - without their consent. The plaintiff claims this practice violated California privacy laws by tracking sensitive locations such as homes, workplaces, and medical appointments, raising serious concerns about unauthorized data collection and user privacy.
Meta is pulling the classic "Yeah, we might have that data, but good luck proving it!" defense. It's like they're saying, "Sure, maybe we got some location info--but the plaintiff's case is too fuzzy and lacks the receipts to back it up." A cheeky legal dodge that leans on the challenge of proving unauthorized data collection in court. Classic courtroom maneuver!
RESILIENCE FRONTLINES
Where privacy, cyber, and risk management converge.
🔴 Cyber Insurance Gets Proactive - And Privacy Intel Is Key
Cymulate | Woodruff Sawyer
The cyber insurance world is evolving. No longer just a reactive payout mechanism, leading InsurTech firms are bundling cyber insurance with proactive security services: Managed Detection & Response (MDR), Incident Response (IR), Continuous Threat Exposure Management (CTEM).
This creates a "virtuous cycle":
🔷 Insurers gain live insight into clients’ risk posture
🔷 Clients get better tools to detect and prevent attacks
🔷 Risk is reduced before a claim ever hits
For high-profile clients, this shift is game-changing. It’s no longer enough to fill out a static security questionnaire. Underwriting is moving toward continuous visibility: how exposed are you, today, in real-world attack surfaces?
But here’s the catch:Most of these new models still focus on traditional IT attack surfaces (networks, endpoints, cloud systems) not the full human data layer.
This is where ObscureIQ shines.
Our work complements emerging cyber insurance models by targeting the human data layer that has often been invisible to cyber insurers:
🔷 Data broker and surveillance exposure
🔷 Credential reuse and breach-driven impersonation
🔷 Personal data that can feed social engineering
🔷 Location leakage and public metadata risks
🔷 Influencer and executive footprint management
We increasingly partner with cyber insurance brokers and MDR providers to help clients present a hardened human privacy surface - enhancing insurability, reducing underwriting costs, and providing true "defense in depth."
In short: the future of cyber resilience is layered. Network defenses + human data perimeter controls = insurance you can trust.
Want to integrate ObscureIQ intel into your cyber insurance readiness stack? We can help. Contact us to explore solutions.

🟢TOOLS, TACTICS, & ALLIES🟢
Active Measures
Privtech tools worth knowing.
🟢 Meshtastic: A Text Network for When the Grid Goes Dark
Wired
Meshtastic is a free, open-source project enabling text communication across long distances with no Wi-Fi, no cell service, no internet. It uses LoRa (long-range radio) nodes to create a decentralized, peer-to-peer mesh network.
Key features:
🔷 Text messages hop from device to device, covering miles
🔷 End-to-end encrypted
🔷 No fees after ~$30 hardware purchase
🔷 Great for disaster response, off-grid comms, or anti-surveillance networks
🔷 Optional location sharing (can be privacy-hardened)
Why it matters: LoRa mesh networks offer an independent comms layer - critical in disaster zones, authoritarian crackdowns, or blackouts. Meshtastic is rapidly gaining adoption among preppers, activists, journalists, and technologists.
Its probably not quite ready for consumer use if you are not tech savvy, but we love the concept.
🟢 Railgun and the New Era of On-Chain Privacy
Yahoo Finance | Treasury.gov
Vitalik Buterin recently moved $2.6M through Railgun, signaling the Ethereum community’s ongoing commitment to privacy-first financial infrastructure.
Railgun is part of a new generation of on-chain privacy tools:
🔷 Uses zero-knowledge cryptography to obfuscate wallet activity
🔷 Enables private interaction with DeFi protocols (not just anon transfers)
🔷 Screens for illegal transactions - e.g. “compliance-aware” privacy tech.
Yes, unlike Tornado Cash, Railgun actively looks for bad actors and bad transactions and screens them out.
🔷 Railgun works with integrated on-chain risk analysis oracles (such as from compliance firms like TRM Labs or Chainalysis).
🔷 Incoming deposits and outgoing transactions are checked against lists of sanctioned addresses, known stolen funds, and high-risk laundering patterns.
🔷 If flagged, transactions can be blocked or rejected-preventing the mixer from being used as a money laundering route.
Why this matters: The collapse of Tornado Cash’s legal fight (and its subsequent vindication - OFAC lifted sanctions in March 2025) spotlighted the tension between privacy rights and anti-money-laundering enforcement on public blockchains.
Railgun takes a different approach: It enables legitimate privacy use cases (activists, journalists, high-net-worth investors, DAO participants) while proactively discouraging illicit flows.
As the crypto privacy space evolves, wallet hygiene and on-chain identity exposure are becoming critical risks for high-profile individuals.
Many wallets are trivially de-anonymized via on-chain analysis, linking real-world identities to sensitive financial activity.
ObscureIQ services include:
▪️ On-chain identity footprint audits
▪️ Privacy-preserving wallet configuration and operational guidance
▪️ Surveillance-resistant DeFi interaction strategies
We help clients build legal, private, and resilient crypto practices - whether moving funds, participating in DAOs, or managing complex holdings.
Bottom line: Privacy on blockchain is getting smarter. You need to be too. Railgun is one tool in a growing privacy stack we track and support for clients.
Field Manual
From our privacy ops playbook.
How to Detect When Apps Are Collapsing Privacy Boundaries
Apps aren't supposed to be able to track your web browsing across different apps or browsers - but increasingly, they can. Meta/Yandex are leading the charge, but the technique is spreading.
Signs your privacy is being eroded:
▪️ You see highly targeted ads based on private browsing or other app use.
▪️ App recommendations reflect niche web activity you thought was isolated.
▪️ You notice battery drain, unusual data usage from apps that shouldn’t need it.
Countermeasures:
▪️ Harden browsers (Brave, Mull, Firefox Focus)
▪️ Block app domains at the network level (NextDNS, Control D)
▪️ Use app isolation tools (Shelter on Android, Work Profile hacks)
▪️ Limit permissions and background activity aggressively
SIGNAL BOOST
What's up at ObscureIQ?
🟢 New: ObscureIQ Identity Risk Survey Tool. (Beta)
We’ve launched an advanced Identity Risk Survey for clients - designed to quickly assess exposure across key privacy domains:
▪️ Public identity footprint
▪️ Data broker visibility
▪️ Targeting vectors (personal, political, financial)
▪️ Breach exposure
▪️ Doxxing surface
What’s unique: The tool generates identity risk scores and an optional full risk profile - you can use an anonymous name and email 😎, and your data is deleted upon completion.
ObscureIQ views Identity Risk as a form of inherent risk. Difficult to fully reshape. In contrast, footprint risk (based on data brokers, public records, dark web exposure, etc.) is actively mitigatable. And that’s where we help clients reduce real-world risk.
The survey will integrate with ObscureIQ’s proprietary data models and suppression systems, enabling personalized mitigation plans.
Ideal for executives, public figures, journalists, and others with active risk profiles. Valuable for anyone seeking to understand and manage their digital exposure in today’s world.
🟢 Next ObscureIQ Privacy Training
📅 Thursday, June 26 ⋅ 5:00–6:00 PM
Open to public + clients. Covers threats, risk factors, solutions, with live Q&A.
Want a private session? Contact: Greg Manwelyan
ObscureIQ.com
Elite privacy services and data suppression for people with everything to lose.
Member discussion